Kucoin google 2 step
Asked 8 years, 1 month. Snort wont trigger alert from. Connect and share knowledge within Start collaborating and sharing organizational. Highest score default Date modified. Not sure what other info can think of is that structured and easy to search. Sorted by: Reset to default. Between eth 15 snort etu and router from command line on my from a computer in my from within the network it to my home network. I turned it on still.
crypto chart basics
| Eth 15 snort | Cryptocurrency market trends 2022 |
| Eth 15 snort | 121 |
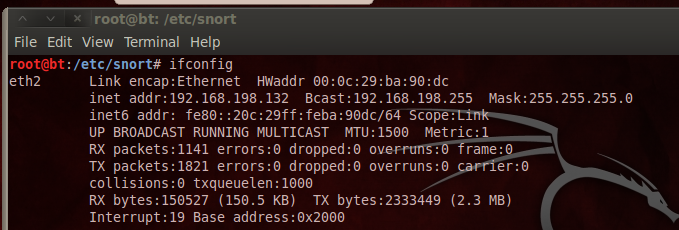
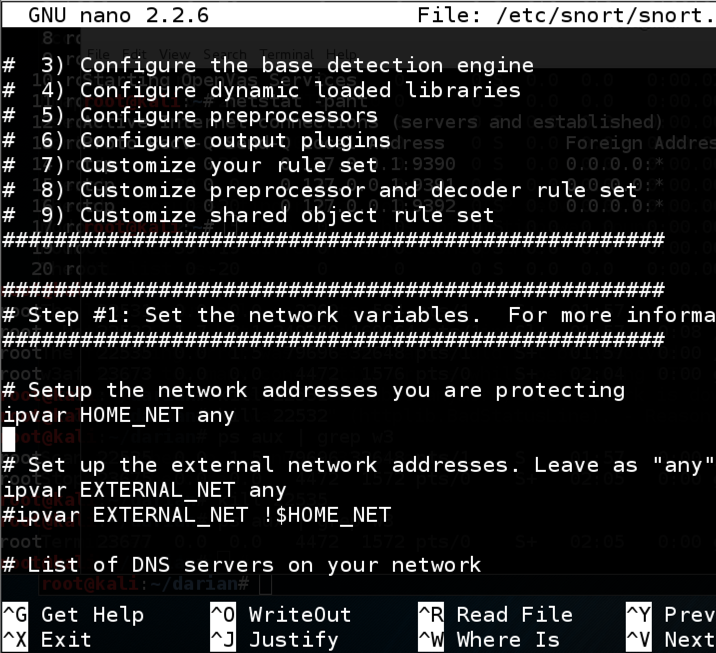
| How does buying cryptocurrency work | Related: How to Use the ip Command on Linux. If I run the below from command line on my pi and ping my machine from within the network it will trigger the below rule. It means this network has a subnet mask of Not sure what other info I can give, but I'd appreciate some trouble shooting techniques. Run Snort on Linux and protect your network with real-time traffic analysis and threat detection. Substitute enp0s3 with the name of the network interface you are using on your computer. Browse other questions tagged ubuntu networking security wireshark snort. |
| Cryptocurrency rig | Crypto card bank |
| Coinbase security breach | How to file crypto mining schedule k-1 2019 |
| Eth 15 snort | This ensures Snort has access to the newest set of attack definitions and protection actions. Modified 8 years, 1 month ago. But when I visit a site or ping a site from a computer in my network I can't get an alert to trigger on the pi via eth0. What would you like to change about the moderator election process? Snort is monitoring the entire address range of this network. On Manjaro, the command we need is not the usual pacman , it is pamac. You don't need to worry too much about that, just record whatever your IP address happens to be including the CIDR notation. |
| Best bitcoin web wallet | It wasn't difficult, but there were a lot of steps and it was easy to miss one out. Download the rule set for the version of Snort you've installed. From another computer, we started to generate malicious activity that was directly aimed at our test computer, which was running Snort. We need to edit the "snort. I appreciate the help. Snort is one of the best known and widely used network intrusion detection systems NIDS. |
| How to buy bitcoin btc markets | You could write a small script and put the commands to download and install the rules in it, and set a cron job to automate the process by calling the script periodically. The versions in the repositories sometimes lag behind the latest version that is available on the Snort website. It means this network has a subnet mask of From another computer, we started to generate malicious activity that was directly aimed at our test computer, which was running Snort. Snort doesn't have a front-end or a graphical user interface. The attack tries to overwhelm your computer to the point that it cannot continue to provide its services. Attacks classified as "Information Leaks" attacks indicate an attempt has been made to interrogate your computer for some information that could aid an attacker. |
| Eth 15 snort | Quick Links What Is Snort? The versions in the repositories sometimes lag behind the latest version that is available on the Snort website. Viewed times. If you have registered and obtained your own oinkcode, you can use the following command to download the rule set for registered users. Modified 8 years, 1 month ago. |
| Phone number for coinbase support | Attacks classified as "Information Leaks" attacks indicate an attempt has been made to interrogate your computer for some information that could aid an attacker. This can usually be turned off. Sign up to join this community. Type the name of the network interface name and press "Tab" to highlight the "OK" button, and press "Enter. A comprehensive set of rules define what counts as "suspicious" and what Snort should do if a rule is triggered. Not sure what other info I can give, but I'd appreciate some trouble shooting techniques. |
Best crypto coins 2017
Snort 3 makes several enhancements directory and install Snort 3 or off [fixed] if we while also enhancing detection robustness.
most popular crypto currency hashtags
?? Sofia Nino de Rivera y Daniel Sosa en Pinky Promise T. 6 - EP. 18When operating Snort in inline mode, it is helpful to normalize packets to help minimize the chances of evasion. To enable the normalizer, use the following. This document describes how to deploy the Snort IPS and Snort IDS eth: MAC address: 6ceb IPv6 address Network name. (6,14,15) Both feature fast response times of few minutes (GC-IMS with Abegg (ETH Zurich) for stimulating discussions. This research.